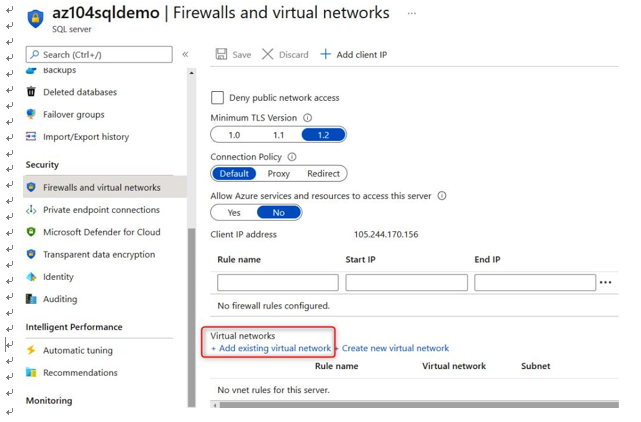
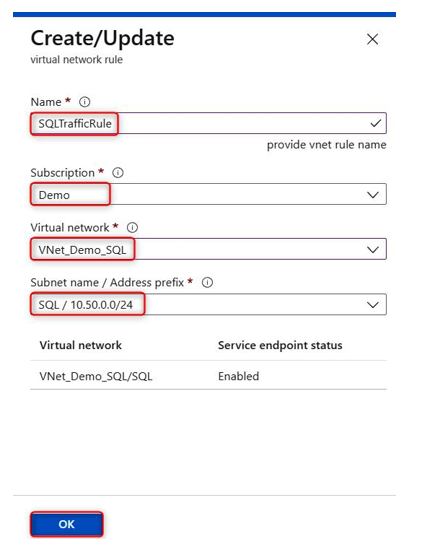
Oct 4, 2021
Deploying Web App service lab – Practice Labs – Deploying and Managing Azure Compute Resources
Deploying Web App service lab
In this lab, you will be guided through the deployment of an Azure container instance with using a Docker image as the source. Finally, you will test connectivity to your containers to prove a successful deployment.
Estimated time: 30 minutes.
Lab method: PowerShell and the Azure portal.
Lab scenario: In this lab, you play the role of an administrator who is looking to utilize Azure App Services for hosting your company’s web applications. Your organization, Contoso, has several websites running in on-premises data centers on servers using a PHP runtime stack. Furthermore, you are looking to start using DevOps practices within your organization and want to use app deployment slots to improve your deployment strategy.
Visit the following URL to the official Microsoft Learning GitHub labs, where you will be guided through each task step by step to achieve the following objectives.
Lab objectives:
I. Task one: Deploy your Web App and Service plan.
- Task two: Create a staging deployment slot for your web app.
III. Task three: Configure deployment settings for the local Git.
IV. Task four: Deploy your staging code.
V. Task five: Swap the staging and production deployment slots.
VI. Task six: Configure autoscaling and test your web app.
Lab URL: https://microsoftlearning.github.io/AZ-104-MicrosoftAzureAdministrator/Instructions/Labs/LAB_09a-Implement_Web_Apps.html.
Lab architecture diagram: The following diagram illustrates the different steps involved in the exercise:
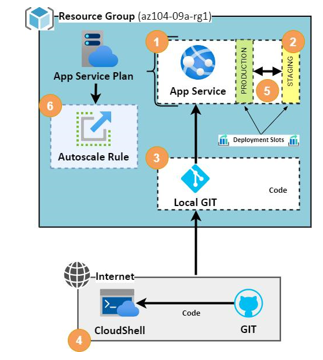
Figure 13.6 – Deploying an Azure web app – architecture diagram
You have now experienced working with Azure web apps on the Azure portal as well as configuring autoscale rules. You should now feel confident in using this service within your daily role. It is best practice to remove unused resources to ensure that there are no unexpected costs.
Summary
In this chapter, we looked at several compute infrastructure type deployments. We explored the deployments of app services, Azure Container Instances, Azure Kubernetes Service, and VM deployments. We also looked at how to scale and manage these systems through a practical demonstration. You should now feel confident in managing Azure compute resources and working with these on Azure.
In the next part of the book, we’ll cover the deployment and configuration of network-related services and components. We will explore the management of Azure virtual networks and securing services. We will then explore the load balancing services available to us, and finally, how to monitor and troubleshoot network-related issues.
More Details