Jan 10, 2023
Securing an app service – Creating and Configuring App Services
Securing an app service
There are several mechanisms you can use to enhance the security of your application on Azure. As part of the AZ-104 exam, we will explore the configuration options that are native to the web application directly. However, note that for real-world implementations, you should investigate additional measures for enhancing the security of your applications, such as employing a firewall – especially a web application firewall – for your web-based applications. These services provide traffic that’s in line with your application and scan for disallowed or heuristic behavior.
In this exercise, we will look at various native application configurations that can be used to increase the security level of your app services:
- Navigate to the App Service plan you worked on in the previous exercise.
- From the left menu blade, under theSettings context, click Configuration. The first tab you will be greeted with is called Application settings. Application settings are variables that are presented securely to your application, but they can be configured externally from the application code. This enhances security by obfuscating the password from code and prevents developers that don’t have RBAC permissions on the Azure portal for the App Service resource from seeing sensitive data, such as secrets that may be stored under Application settings. The other item that can be configured is Connection strings:
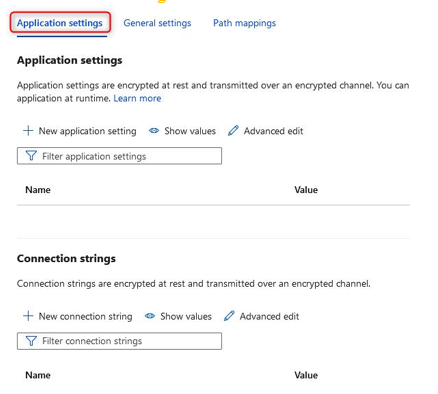
Figure 12.22 – Application settings
- The next tab is General settings. Here, you will want to ensure File Transfer Protocol (FTP) traffic is conducted securely if it’s allowed by your organizational policies. FTP is a technology that enables file transfer operations for your systems. It is commonly used by developers to upload code to the system; an alternative, as we explored in the previous chapter, is to use a source code repository such as Git. The most secure option is to disallow all FTP-based traffic as prevention is better than a cure. However, since many applications require developers to be able to upload their code, changing the FTP transfer protocol that’s being used is the next best option. Setting traffic to FTPS only ensures that the FTP traffic is conducted over an HTTPS tunnel, meaning that all the data is encrypted. So, even if it is intercepted, it is less likely to be compromised. Set this to FTPS only for
this exercise:
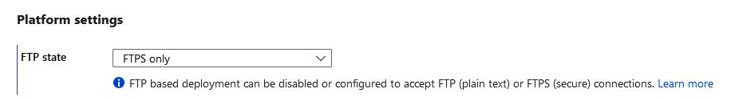
Figure 12.23 – FTP state
- Click Save at the top of the screen:

Figure 12.24 – Options menu
Note that after clicking Save, you will be warned that the application needs to be restarted.
- The last tab that can be configured in the General settings menu is Path mappings. We won’t explore this here.
- From the left menu pane, clickAuthentication. This blade contains the configuration settings related to authentication, the type of identity provider service that’s being used, and the authentication flow. To explore the available configurations, click Add identity provider:
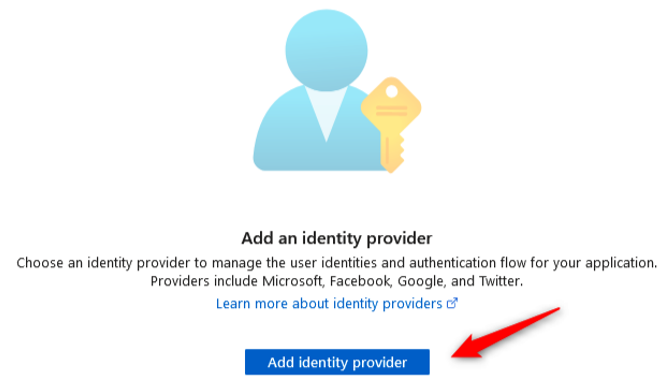
Figure 12.25 – Add identity provider
- At the time of writing, you can choose from several identity providers – that is, Microsoft, Facebook, Google, Twitter, and OpenID Connect. ClickMicrosoft:
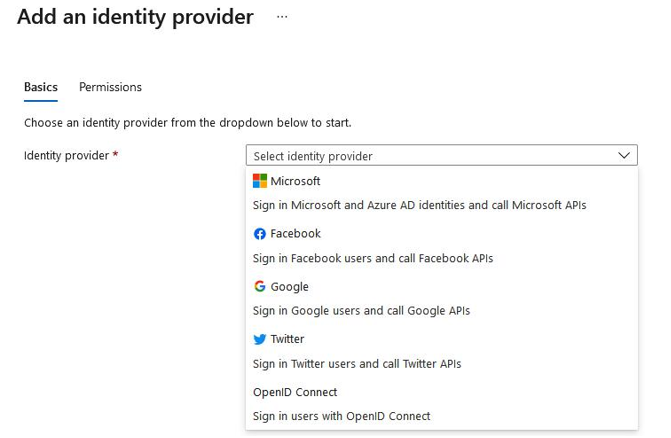
Figure 12.26 – Add an identity provider
More Details