Feb 5, 2024
Security – Creating and Configuring Containers
Security
When configuring your network for AKS, you should consider the security components that also impact your design and management decisions. There are several items to consider (which we discuss in the following sections) that can improve the security of your containers.
Enabling a private cluster
For enhanced security, you can enable a private cluster. This ensures that trafficbetween your application programming interface (API) server and node pools is conducted over private network paths only. When configured, the control plane (API server) is run within the AKS-managed Azure subscription while your AKS cluster runs in your own subscription. This separation is key. Communication will thenoccur over a private endpoint (private link) from your AKS cluster to the private link service for the AKS VNet.
Setting authorized IP ranges
These are ranges that you will limit to accessing your AKS cluster. This can be specified as a single IP, as a list of IP addresses, or as a range of IP addresses in classless inter-domain routing (CIDR) notation.
The following screenshot is an example of setting authorized IP addresses:
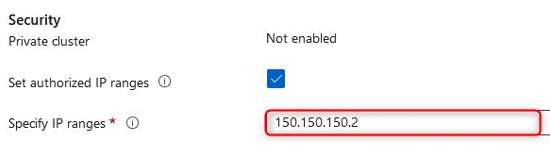
Figure 11.61 – Authorized IP addresses
You now understand the role that authorized IP ranges play in your AKS deployment.
Next, we will explore the impact that network policy has on deployments.
Network policy
This is used tomanage traffic flow between Pods in an AKS cluster. By default, alltraffic is allowed, and by utilizing network policy, you enable the mechanism to manage this traffic using Linux iptables. Two implementations can be followed: Calico and Azure Network Policies. Calico is an open source solution provided by Tigera, whereas Azure has its ownimplementation of the same type of technology. Both services are fully compliant with the Kubernetes specification. The choice of network policy provider can only be chosen on the creation of the AKS cluster and can’t be changed, so it’s pivotal that you understand the differences between the solutions prior to making your choice.
The key differences between the solutions are presented here:

